Critical vulnerability in Azure Cosmos DB – Act now!
Last Thursday, August 26, Microsoft informed thousands of its Azure customers about a critical vulnerability in their cloud offering Cosmos DB. Wiz, the company that found the #ChaosDB security vulnerability, was able to extract any other Cosmos DB customer’s primary key via the Jupyter Notebook integration.
What happened
- On August 9 the research team of Wiz found the security vulnerability in the Jupyter Notebook integration of Azure Cosmos DB
- On August 12 Wiz informed Microsoft about the security issue
- Microsoft’s security team took immediate action and disabled the vulnerable feature within 48 hours
- On August 26 Microsoft informed potential customers
The Vulnerability
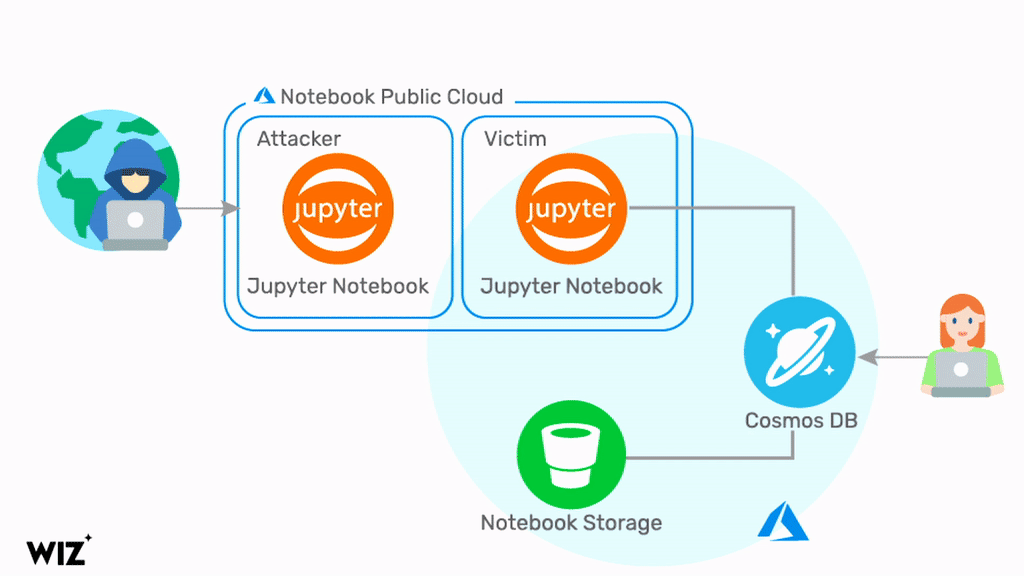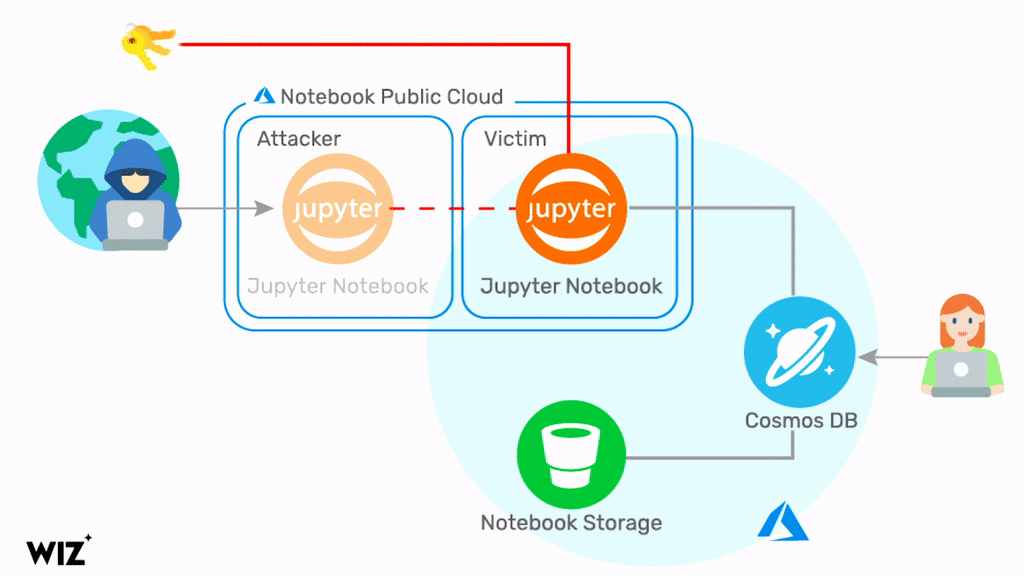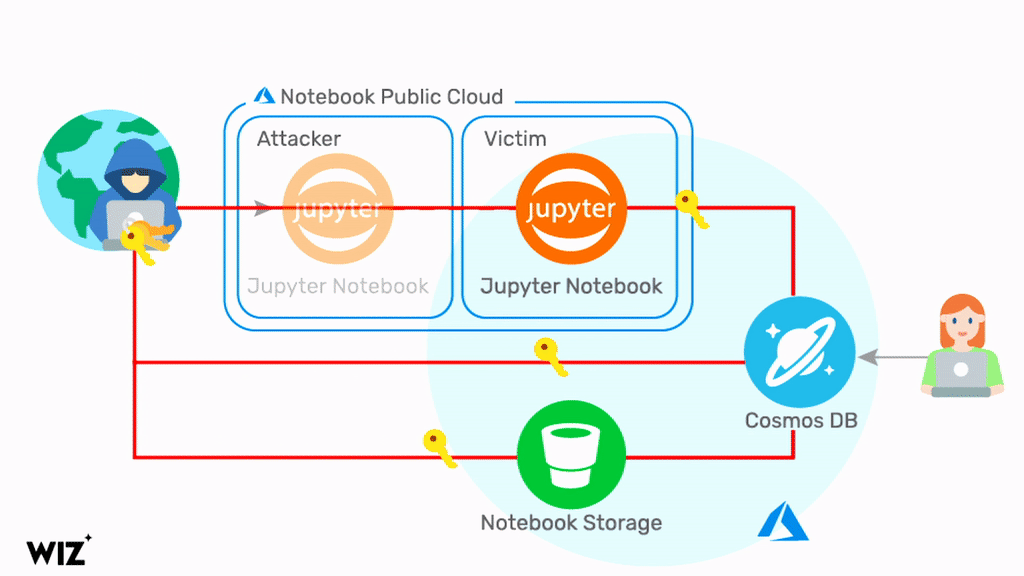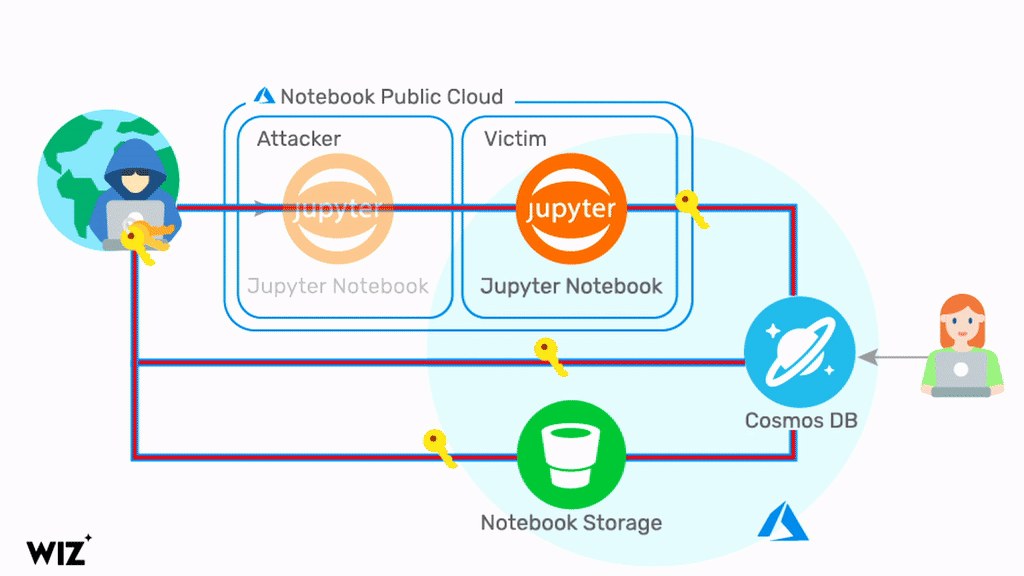
Wiz was able to exploit a chain of security vulnerabilities in the Jupyter Notebook integration of Azure Cosmos DB. By doing so, they were able to obtain a set of credentials related to the Cosmos DB account, the Jupyter Notebook compute resource, and the Jupyter Notebook Storage Account, including the primary key. With these credentials, Wiz was able to view, modify, and delete data in the Cosmos DB account.
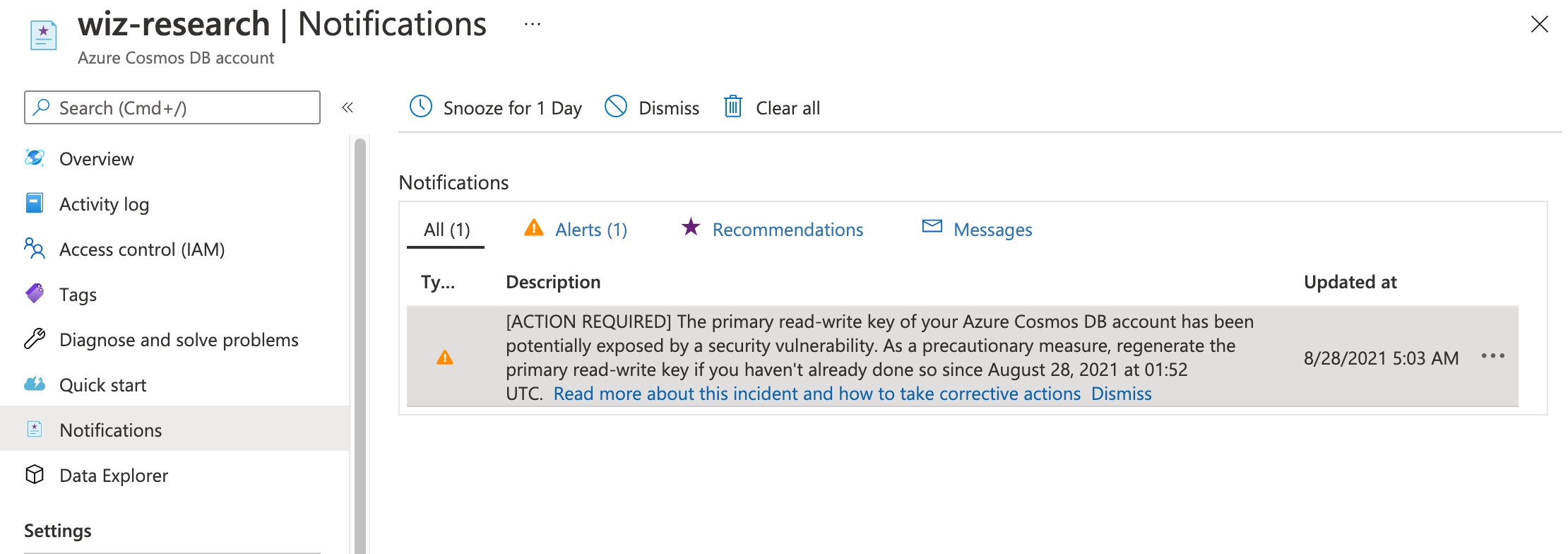
Am I impacted?
If your organization is using Cosmos DB it is likely that you are impacted by this vulnerability. Every Cosmos DB account that uses the notebook feature, or has been created after January 2021, is potentially at risk. You can review your Cosmos DB account notifications to verify whether you are impacted.
“Microsoft notified only customers that were affected during our short research period (around a week). We think the actual number of potentially impacted customers is much larger and probably includes the majority of Cosmos DB customers, as the vulnerability has been present for months.”
Wiz, https://chaosdb.wiz.io
Furthermore, Wiz mentions that Microsoft has no indication that external entities outside of the researchers of Wiz had access to the primary key of Azure Cosmos DB accounts. Microsoft is also not aware of any data access because of this vulnerability as mentioned here.
Azure Cosmos DB accounts with virtual network integration or firewall enabled are also protected from any unauthorized access. That said, the secret itself might have been compromised.
Act now!
As mentioned Microsoft disabled the vulnerable feature within 48 hours. This means the vulnerability cannot be actively exploited anymore.
Due to the primary key being a long-lived secret you will have to recreate or manually rotate it. Based on your current implementation you might be able to rotate the primary key without any downtime. You will find further details on how to recreate and rotate your key in the Cosmos DB documentation.
Further improve security
You can further improve the security of your Cosmos DB account by implementing one of the following network security features:
- Enable the IP firewall feature to only allow certain IPs to access your Cosmos DB account
- Restrict access to your Cosmos DB account to virtual networks in your environment
- Configure a fully private Cosmos DB account by using Private Link
Furthermore, you should rotate your Cosmos DB account keys on a regular basis.
More details
You will find more details on the ChaosDB Vulnerability here:
- https://chaosdb.wiz.io
- https://www.wiz.io/blog/chaosdb-how-we-hacked-thousands-of-azure-customers-databases
- https://www.reuters.com/technology/exclusive-microsoft-warns-thousands-cloud-customers-exposed-databases-emails-2021-08-26
Also don’t miss this Youtube video by Wiz: